CoSoSys Endpoint Protector DLP 5.1.0.2 allows Host Header Injection
INTRODUCTION
CoSoSys is a leading developer of endpoint centric Data Loss Prevention (DLP) solutions and security software. Its flagship product, Endpoint Protector, is an advanced all-in-one DLP solution for Windows, macOS, and Linux computers. The solution puts an end to unintentional data leaks, protects from malicious data theft, offers seamless control of portable storage devices, and helps to reach compliance with data protection regulations such as GDPR, HIPAA, CCPA, or PCI DSS. It provides a short learning curve and flexible modules that can be mixed and matched to a customer’s needs. The solution has functionalities such as Device Control, Content and Context Aware Protection, eDiscovery, and Enforced Encryption.
CoSoSys’ mission is to enable businesses around the world to take full advantage of the performance benefits of mobility, portability, and communications solutions, without compromising security. It is available directly to North American customers and distributes its products globally through partners and resellers. Endpoint Protector was recognized in the 2017 Gartner Magic Quadrant for Enterprise Data Loss Prevention. The company has offices in Romania, Germany, and the USA.
Vulnerability: Host Header Injection (cwe-20)
Product :
Endpoint Protector (CoSoSys Ltd)
Affected Component:
> Endpoint Protector 5.1.0.2.Virtual.Appliance.OVF
> Endpoint Protector 5.1.0.2.Virtual.Appliance.OVA
> Endpoint Protector 5.1.0.2.Virtual.Appliance.VHD
> Endpoint Protector 5.1.0.2.Virtual.Appliance.PVM
Remediation: The web application should use the SERVER_NAME instead of the Host header. It should also create a dummy vhost that catches all requests with unrecognized Host headers. This can also be done under Nginx by specifying a non-wildcard SERVER_NAME, and under Apache by using a non-wildcard serverName and turning the UseCanonicalName directive on.
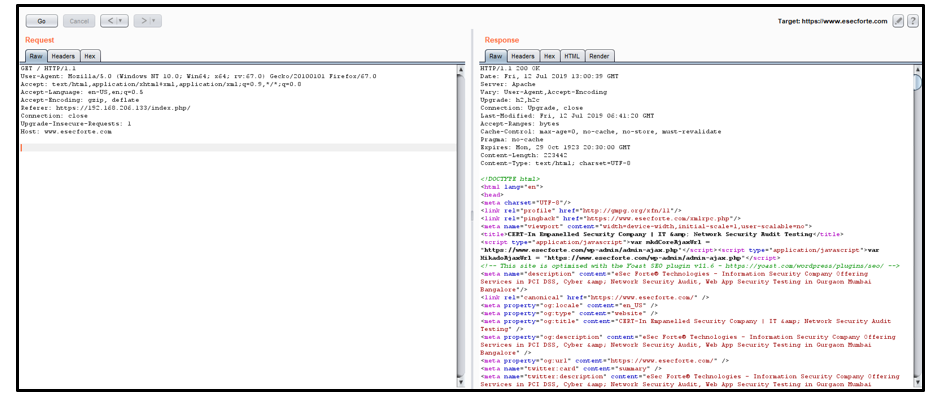
Impact : In many cases, developers are trusting the HTTP Host header value and using it to generate links, import scripts and even generate password resets links with its value. This is a very bad idea, because the HTTP Host header can be controlled by an attacker. This can be exploited using web-cache poisoning and by abusing alternative channels like password reset emails.
[Reference]
> https://www.endpointprotector.com/
> https://www.endpointprotector.com/products/endpoint-protector
> [Discoverer]
> Shashank Chaurasia from eSecForte Technologies Pvt Ltd
EPP HOST HEADER INJECTION POC
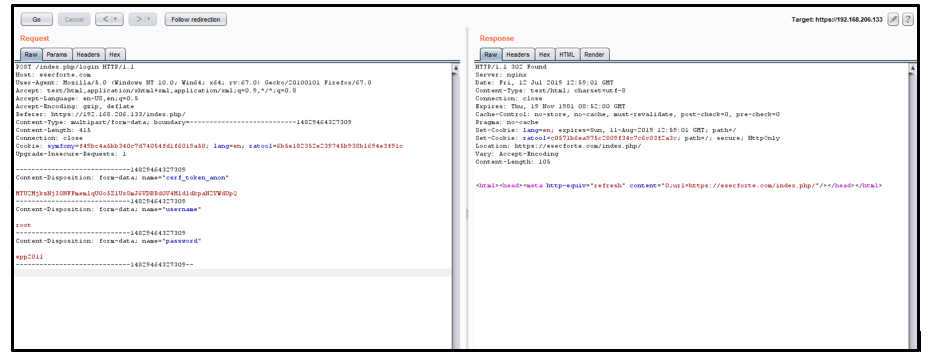
1. Login to the application using default password: – “root:epp2011”
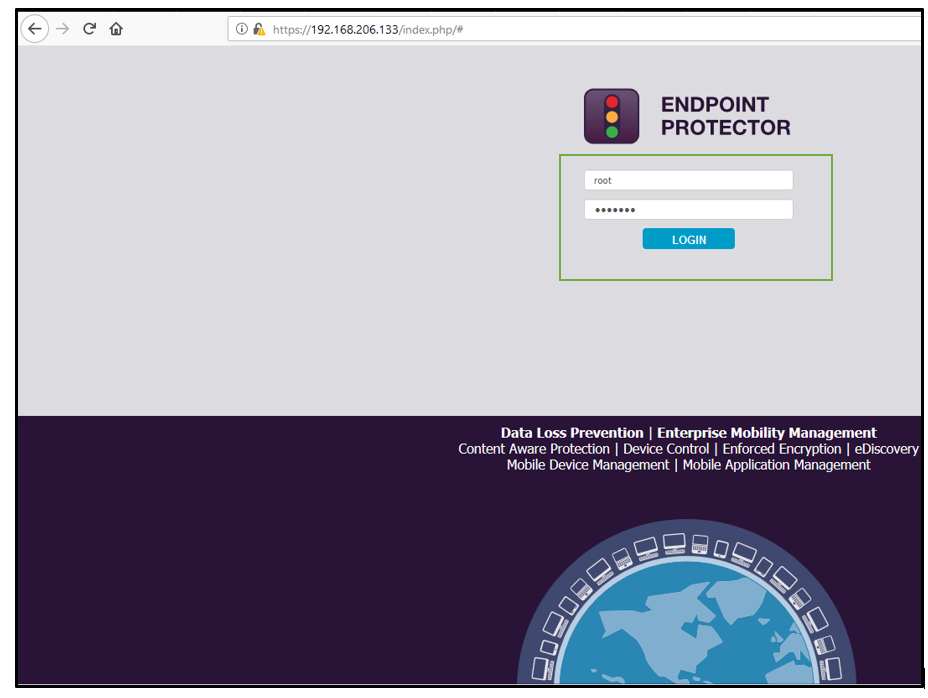

2. Intercept the request while logging in through any proxy tool:
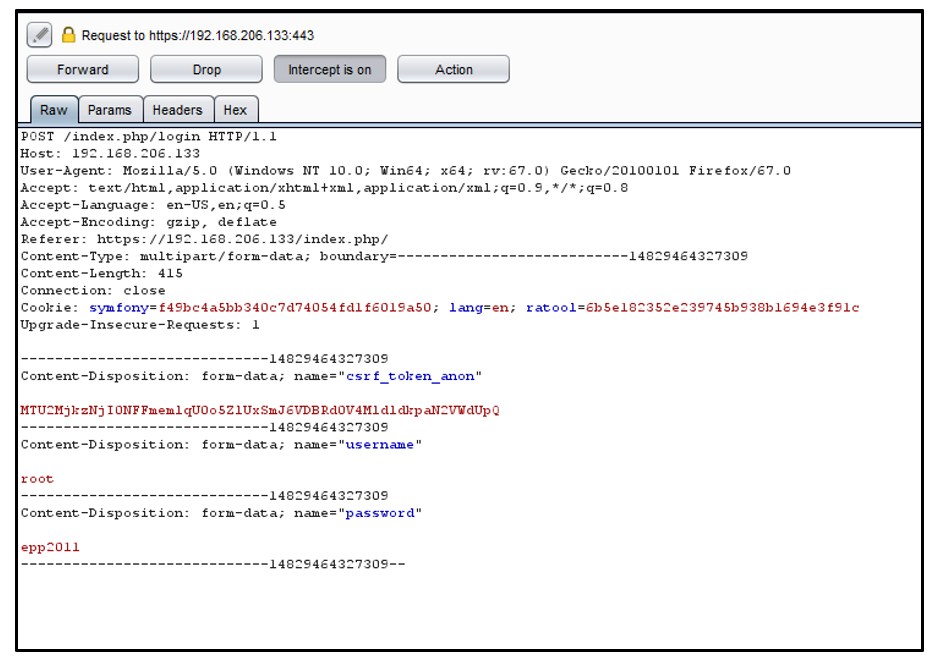

3. Change the host header from Server IP to www.esecforte.com and send it.
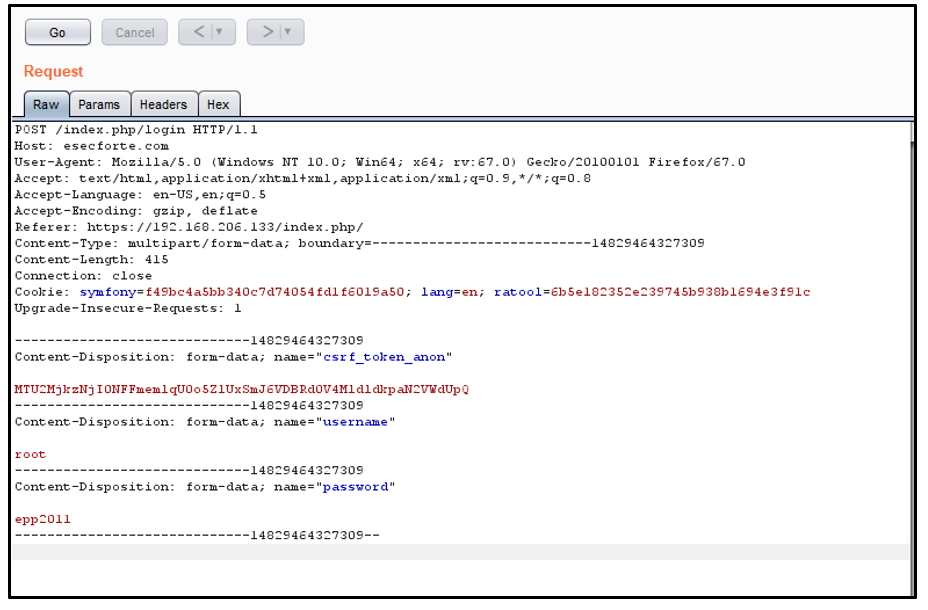

4. Now click on follow re-direction:

5. Again, click on follow re-direction
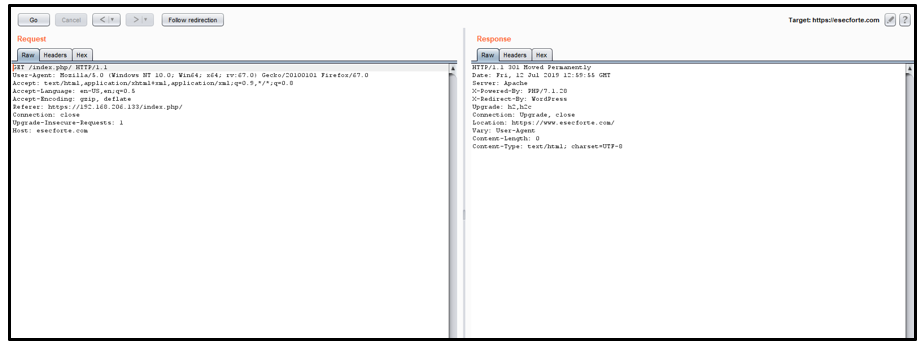

6. Here you can see that host header injection is successful