Second Order SQL Injection
Second Order SQL Injection :-
I always thought that escaping single quotes in a string based user input used for database transactions will prevent SQL injections..but this is not always the case when single quotes are escaped inconsistently (as we will see in this blog).
Say hello to SQL injection of the second order !
Basically second order SQL injections take place when one functionality of a web application takes a user input from a user, escapes (not strips) all SQL metacharacters and inserts that data input into a database. Next, some other functionality of the same application uses that data to craft another SQL query to do a database transaction without escaping that data first (bad idea!). The database transaction done by the second functionality introduces a SQL injection bug in the web application known as second order SQL injection.
I have’nt heard of any Second Order SQL Injection Attacks on real world targets, so decided to make up an example attack myself. Following are the two functionalities with their respective codes (select.php and insert2.php).
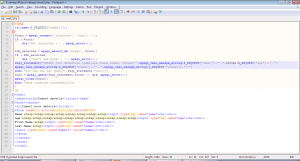
The first functionality inserts data into the database. The second functionality uses the data inserted into the fname column to craft a SQL query and get data from the database and show it on the frontend. For making it easy to understand, all the SQL queries run by the web applications are also shown on the frontend.
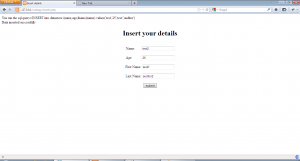
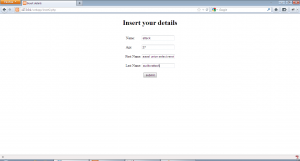
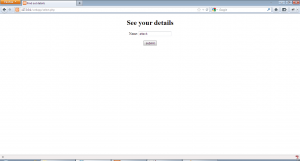
Lets do a basic walk through of the applications. First using insert2.php, our details are inserted as shown:-
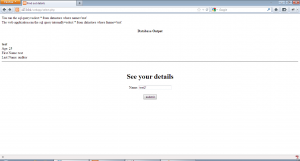
As we can see from the second pair of examples, this application escapes any single quotes while inserting data into the database. Now, lets use select.php to get the inserted data.
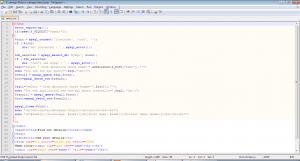
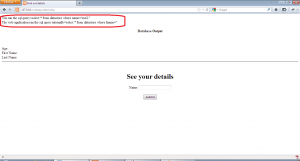
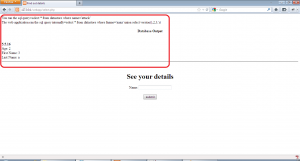
This application also escapes the user input as shown, queries the database using that value. The fname value we get from the first query is used to run another query to get all the data about a user. We can see from select.php code that the second query does not escapes the fname value returned from the database and uses that value directly to get all data. This is the point of our second order SQL injection.
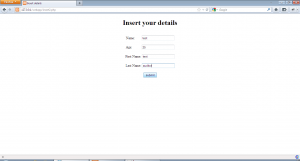
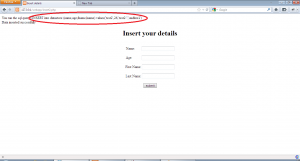
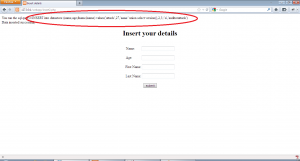
So to manipulate the second query of this application in a meaningful way, we will have to inject a SQL query in the first name field of insert2.php and make sure the query is correctly formed and then use select.php to trigger the vulnerable query. We open the application insert2.php and inject the value ” aaaa’ union select version(),2,3,’a ” in the first name field as shown:-
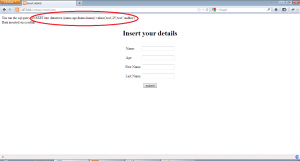
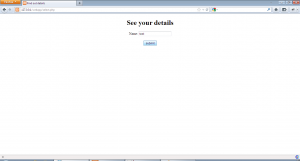
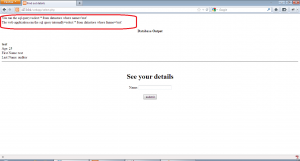
Now, we open select.php and insert the name “attack” and hit enter to get the following:-
Allright!! we were able to exploit the vulnerability to run an arbitrary query on the database. Similarly, we can use advanced SQLi to gain unauthorized access to the database.
The way that the application was vulnerable to second order SQLi is very unlikely in real world and this was only used to demonstrate the exploitation of this vulnerability. Hope the explanation was clear and everyone liked it 🙂
Cheers!!
eSecForte is the Authorized Distributor/Reseller of Rapid7 Security Products in India, Bangladesh & Srilanka
See More eSecForte’s Information Security Solutions :-
- Core Impact – Penetration Testing Tool
- CHECKMARX- STATIC APPLICATION SECURITY TESTING
- HP WEBINSPECT : APPLICATION SECURITY TESTING
- Netsparker Web Application Security Scanner
- Burp Suite- Web Security Testing Software
- NESSUS VULNERABILITY SCANNER TOOL
- TENABLE.IO VULNERABILITY MANAGEMENT
- TENABLE SECURITYCENTER Vulnerability Management
- Vulnerability Scanning and Vulnerability Management
- Vulnerability Assessment and Penetration Testing (VAPT)
- WEB APPLICATION SECURITY SERVICES