Tenable.IO Vulnerability Management
Tenable.IO is the first Cyber Exposure platform to protect any asset on any computing platform



Tenable.IO: Overview
Tenable.IO provides you support with the development of the application, which further aids you in understanding your cloud’s security needs and also provides support with Tenable.IO vulnerability management. There is no need to club all these applications as Tenable provides you an option to purchase these individually according to your needs.
In order to mitigate cybersecurity risks, companies around the world are not only relying on their IT team but are also taking help from the cyber experts Tenable. There are more than 20000 organizations around the globe today which are dependent upon them for their company’s data security.
Why Tenable.IO?
Features of Tenable.IO
Types of Tenable.IO
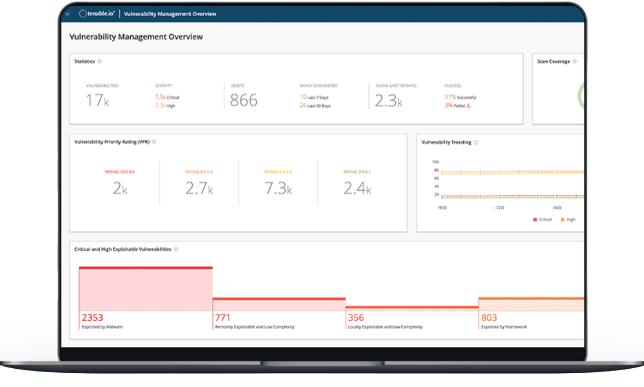
Tenable.IO Vulnerability Management
With the evolving IT scenario, organizations are also looking for enhanced vulnerability management tools. IT systems today are a mix of traditional and modern technology. The age-old scanning techniques are not suitable today and do not solve any purpose.
Organizations today are looking for asset-based vulnerability management tools that help in prioritizing vulnerabilities. They need something that can analyse and provide a quick resolution to the risk.
With the well-focused approach and streamlined task, it provides you an enhanced vulnerability management application. It helps the security teams to improve their efficiency and aids them in prioritizing tasks. It uses algorithm-based models and provides information about the asset-based vulnerabilities.
Tenable.IO Web Application Scanning
The development of complex web applications has increased the risk of cyber-attacks. Developers are designing applications that require enhanced monitoring to avoid any loopholes. One single security product is not enough to save this data which can be left in open and at an increased all-time risk.
Tenable.IO web application scanning helps you understand the application and provides you a roadmap to go further in terms of data protection. It provides you complete web scanning of all your web applications and leaves no room for any manual scanning which might be in the virtue of missing out on something important. It provides you the maximum success ratio as compared to any other web scanning technology.
To enhance the performance of the web application, there are certain parts which are not deemed fit for scanning, Tenable.IO web application scanning tool can easily differentiate between the two and excludes the ones which are not fit for scanning. It is completely automated and hardly requires any manual intervention. Tenable.IO web application scanning not only provides you scanning support for modern applications but also supports you with traditional ones like HTML.
Container Security
With the advancement in container-based apps, the risk associated has also increased. Security teams in almost 75% of the organizations today are struggling to understand these container based-applications and to develop solutions to mitigate the risk involved.
The existing security patches and features are not enough for the container-based applications. Tenable.IO provides the IT teams visibility into the blind spots which they might have missed and provides clear visibility of Docker container image, thus providing an insight into malware detection even before it is implemented. With pre-visibility, it becomes easier for the teams to work around a particular task and developers get a clear picture of what is required to create a shield against the detected malware.
With the ever evolving technology development today, Tenable.IO container security helps you track down vulnerabilities proactively and helps you solve complex security challenges.
How to buy Tenable.IO
Tenable.IO is a subscription-based product and once activated it cannot be returned. The product can be purchased through the reliable and trusted value added partner Esec Forte, who is catering to 1000 plus organizations. Upon making the payment, an activation email is sent to your email id with a URL which leads you to a support portal from where you would get an activation code. The subscription is valid for a period of 1 year and needs to be renewed post expiration.
Contact us today to learn more about our products and services.
We are headquartered in Gurugram & Regional Offices in Mumbai, Delhi, Bangalore – India.