Endpoint Protector
Endpoint protector: Award wining software tool ode to data loss Prevention.
Endpoint Protector Data Loss Prevention Tool
Data theft and unintentional data leaks are unexpected obstacles that any organisation can face. A comprehensive security solution that provides control of all storage devices including the portable ones is a boon to an end user. Endpoint Protector is much more than a security solution.
Introduction: What is an endpoint protector?
An endpoint protector is a software approach whereby end users of a network are given limited access or conditional access to the business through various sets of conditions and provisioning.
Endpoint protector, the Data Loss Prevention (DLP) tool can be used across platforms, and it ensures complete control of multiple hardware ports. This tool can work on various software like Windows, Linux, iOS, etc. from data theft and threat through various end-user devices like mobiles, tablets, laptops, POS (point-of-sale) terminals, etc. during transfer of data, online processing, etc.
This tool has an added advantage of scanning data in motion and at rest. By administering total encryption, it offers thorough mobility management.
Schedule a demo with us
You can connect with us for live product Demo and more information
How does the Endpoint Protector Works?
Features of Endpoint Protector
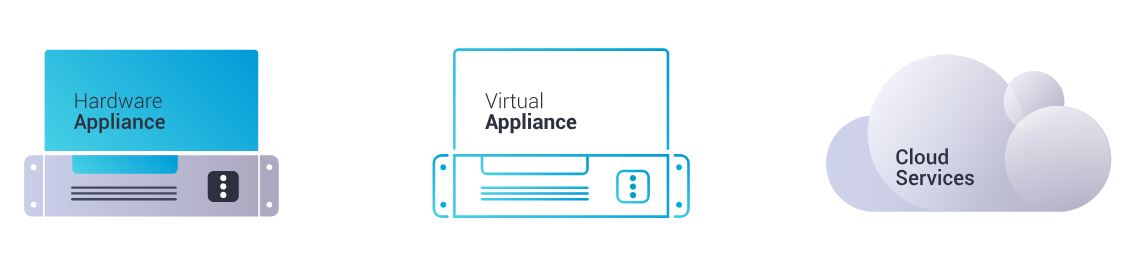
Available as Hardware Appliance, Virtual or through Cloud Services

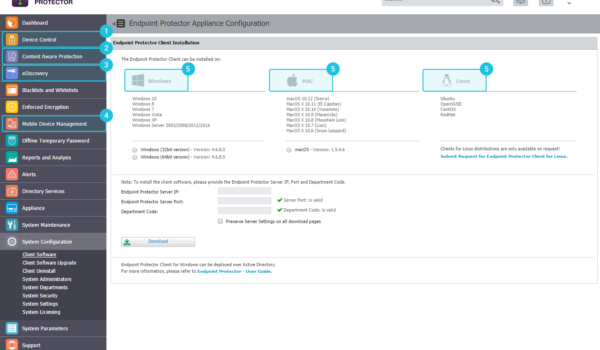
Endpoint Protector Dashboard

My Endpoint Protector
Request a Demo
eSec Forte Technologies is an Cert-In Empanelled | CMMi Level 3 | ISO 9001:2008 | ISO 27001-2013 certified Cyber Security and IT Services Company, Having headquarters in Gurugram, Mumbai, Bangalore, Delhi– India, Singapore & Sri Lanka. We are Value Added Partner of Endpoint Protector
Benefits of Endpoint Protector Data Loss Prevention Tool
Customer reviews
Endpoint Protector Pricing
Endpoint Protector price is dependent upon the license you wish to choose as it gives you various options. The detailed structure can be availed through trusted partner eSec Forte Technologies who are well versed with all the data associated. The endpoint protector pricing is done in a way as to ensure professional finesse. Contact us for information on pricing.
We are headquartered in Gurugram, Mumbai, Delhi & Bangalore – India. Contact our sales team @ +91 124-4264666 you can also Drop us email at [email protected] .
We Want to Hear from You !!
Contact us today to learn more about our products and services.